One of the most popular computer manufacturers Lenovo is being
criticized for selling laptops pre-installed with invasive marketing
software, or malware that, experts say, opens up a door for hackers and
cyber crooks.
The software, dubbed ‘Superfish Malware’, analyzes users’
Internet habits and injects third-party advertising into websites on
browsers such as Google Chrome and Internet Explorer based on that
activities without the user’s permission.
Security researchers recently discovered Superfish Malware presents
onto new consumer-grade Lenovo computers sold before January of 2015.
When taken out of the box for the first time, the adware gets activated
and because it comes pre-installed, Lenovo customers might end up using
it inadvertently.
SUPERFISH CERTIFICATE PASSWORD CRACKED
The Superfish Malware raised serious security concerns about the company’s move for breaking fundamental web security protocols, carrying out "Man in the Middle"
(MitM) attacks - impersonating the security certificates of encrypted
websites in order to monitor users’ behavior even on protected sites.
This would trouble Lenovo users because MitM attack can open a door for
hackers to potentially compromise the sensitive information of any
customer affected by Superfish - like passwords or banking details -
because users’ data isn't actually being protected.
Anyone with the password that unlocks that single password-protected
certificate authority would be able to completely bypass the computer's
web encryption.
According to a post
by Errata Security's Robert David Graham, he cracked and published the
password which was stored in the Superfish software's active memory and
was trivial to extract. So, one could imagine the loss, if the same
would be done by any hacker or cyber crook.
SUPERFISH MALWARE TEMPORARILY REMOVED
After the news fired up over the Internet and multiple users complained
of popups and other unwanted behavior, the computer giant removed the Superfish Malware.
"We have temporarily removed Superfish from our consumer systems until such time as Superfish is able to provide a software build that addresses these issues. As for units already in market, we have requested that Superfish auto-update a fix that addresses these issues," a Lenovo community administrator, Mark Hopkins, wrote in late January.
Hopkins also defended the company from criticism over installing
Superfish in the first place — but it didn't address the false HTTPS
certificate problem. He also says that Lenovo users can refuse the terms
and conditions when setting up their laptop in order to disable the
software.
"To be clear, Superfish technology is purely based on contextual/image and not behavioral," Hopkins’ statement reads. "It does not profile nor monitor user behavior. It does not record user information. It does not know who the user is."
SELF-SIGNED HTTPS CERTS RAISED MAJOR SECURITY CONCERNS
While other users on online forums are reporting that Superfish Malware actually
installs its own self-signed certificate authority which effectively
allows the company to snoop on secure connections. And if true, Superfish Malware could be far more dangerous than we had thought.
"A blatant man-in-the-middle attack malware breaking privacy laws. I have requested return of the laptop and refund as I find it unbelievable that ... Lenovo would facilitate such applications pre bundled with new laptops," the user wrote on the Lenovo forums.
Facebook engineering director Mike Shaver also warned about the invasive
adware via his personal Twitter account, saying that he found SuperFish
certificates posted by different users who had shared the same RSA key.
"Lenovo installs a MITM cert and proxy called SuperFish, on new laptops, so it can inject ads? Someone tell me that's not the world I'm in," Shaver tweeted.
LENOVO - IT’S JUST TO ENHANCE USERS’ EXPERIENCE
The company this morning issued a weird statement addressing the
controversy on the Lenovo computers. According to the computer giant,
the Superfish software was "to help customers potentially discover interesting products while shopping."
"The relationship with Superfish is not financially significant," the statement reads. "Our goal was to enhance the experience for users. We recognize that the software did not meet that goal and have acted quickly and decisively."
What was my reaction on the fresh statement issued by the company? Oh!
Come on Lenovo, we know the reality. May be you are one of the world’s
largest PC brands, but after all you are also a Chinese PC brand.
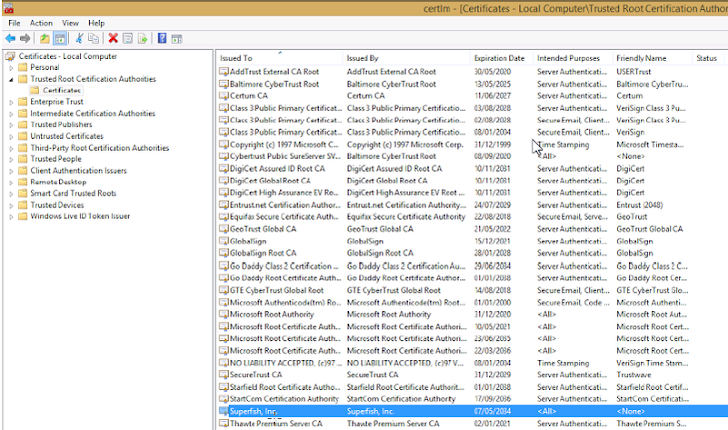
HOW TO REMOVE LENOVO SUPERFISH
HOW TO REMOVE LENOVO SUPERFISH
In order to remove Lenovo Superfish Malware from your system, run the
Microsoft Management Console (mmc.exe), and do the following:
- Go to File and Click Add/Remove.
- Choose Certificates, click Add.
- Choose Computer Account, click Next
- Choose Local Computer, click Finish
- Click OK
- Look under Trusted Root Certification Authorities -> Certificates
- Find the one issued to Superfish and delete it.
LENOVO’S BAD HISTORY REGARDING BACKDOOR
This isn't first time, in past the computer giant was caught installing malware backdoors in its products and was also banned by different countries for same reasons.
In the mid of 2013, the spy agencies - the ‘five eyes’ alliance of the
US, Britain, Canada, Australia, and New Zealand - banned Lenovo for
allegedly installing backdoor into Lenovo-brand circuit boards, along
with other vulnerabilities discovered into the firmware.

No comments:
Post a Comment